In this video, we take a deep dive into configuring Windows Hello for Business (WHfB) using Microsoft Intune passwordless authentication using dual Multi-Factor Unlock using both PIN and Facial recognition for extra security on the end user Windows device.
This is a hybrid environment where on-premise active directory is synced to EntraID using Entra Connect sync.
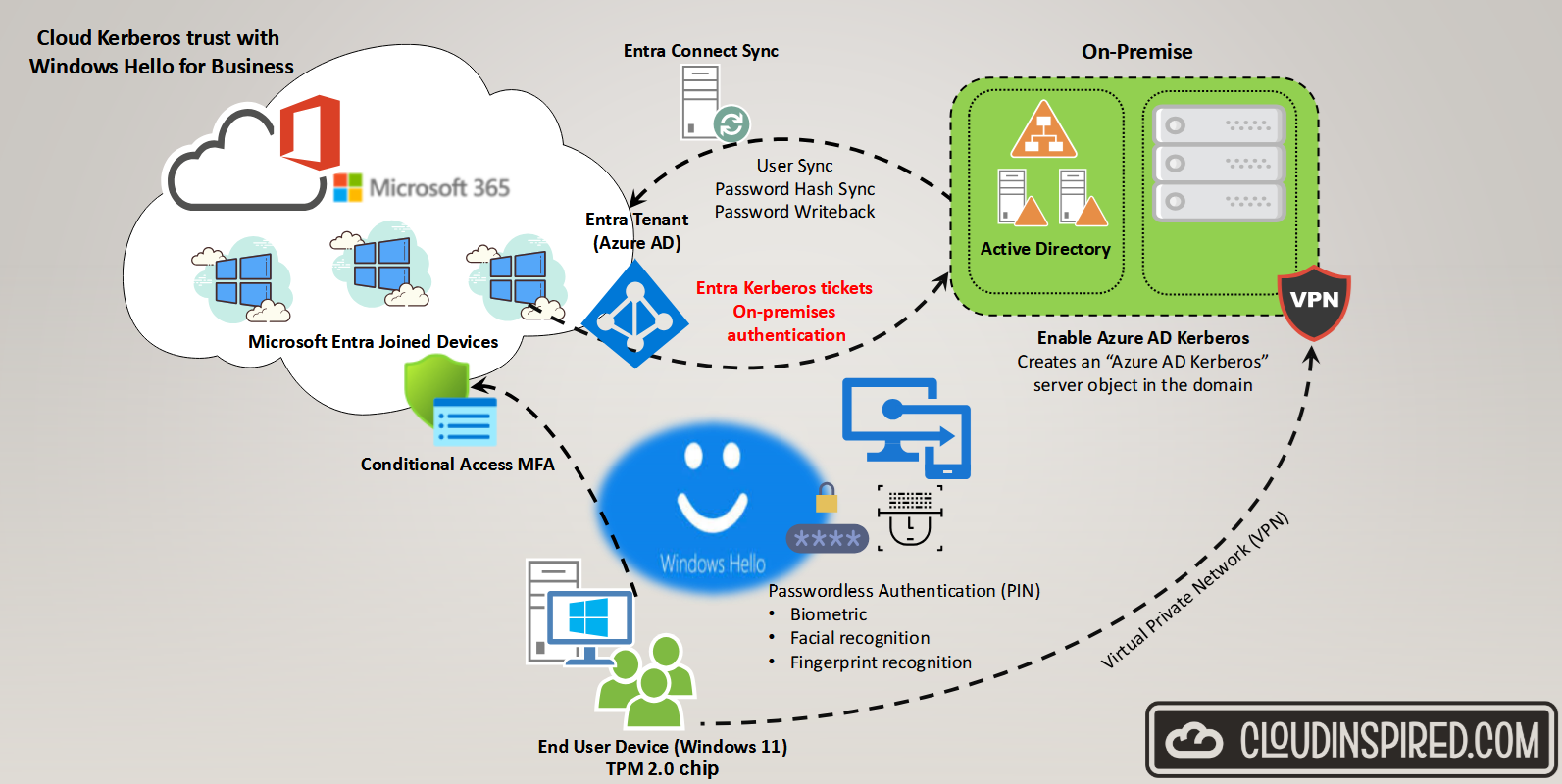
One of the problems with Windows hello and using passwordless and PIN authentication is accessing traditional file shares etc and authenticating with Domain Controllers on premise. The single biggest issue during initial deployment is where a synced user identity is required to authenticate to a hybrid environment. We have our internet end user Windows 11 device, enrolled as a Entra ID Joined device, a cloud only device (not domain joined) and managed by Intune but you want the user to still access resources within your domain over a VPN or when in the office over a LAN. This is where cloud Kerberos trust comes into action where we create a Azure AD Kerberos server object in the Active Directory domain.

This will enable us to authenticate using Microsoft Entra Kerberos to request Kerberos ticket-granting tickets and access on-premise file shares. This eliminates the need for any complex PKI public key infrastructure using certificates to deliver a simple solution to access.
Contents of this video using Windows Hello for Business
- Intro
- Basic Windows Hello for Business (WHfB) settings in Intune
- User / Device Group for WHfB
- Advanced Intune Settings for WHfB using Profiles
- Intune Multi-Factor Unlock PIN and Facial
- Conditional Access enable MFA as part of your device registration process
- Inactivity Device Lock
- Test Multi-Factor Unlock on Device
- Accessing On-Premise resources with WHfB
- Enabling Entra ID Kerberos for hybrid identities
- Cloud Kerberos Trust using Intune policy (not OMA-URI) pre-defined settings
- Test Windows 11 accessing On-Premise share







