Step by step guide explaining how to setup and configure a Azure VPN gateway (point to site) connection with RADIUS, NPS and Azure AD Multi Factor Authentication MFA Extension. Showing the configuration allowing a secure IPsec VPN tunnel to be created from client devices to an Azure Virtual Network.
Azure VPN Point-to-Site Diagram
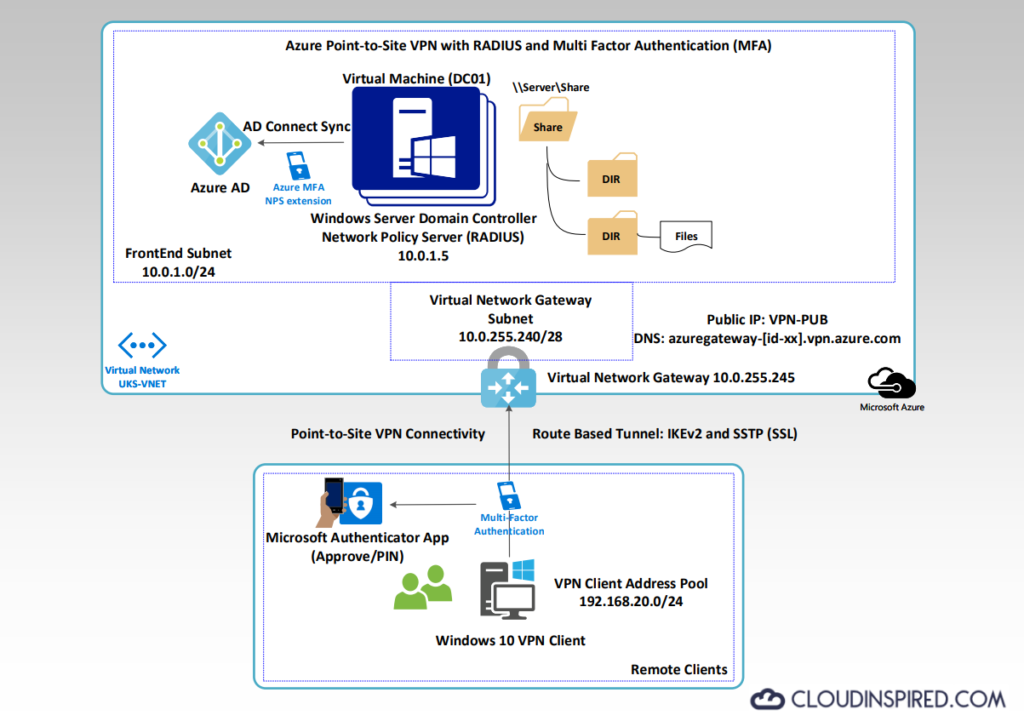
This is a great solution for company users who need to connect to an Azure network from home, during the covid 19 pandemic, remotely and outside the office over a internet connection. The video shows a diagram, where the user has a Windows 10 device and is able to login to the Azure VPN using Active Directory credentials that are also synced to Azure AD. Azure AD Multi factor NPS extension is also installed so the user is required to login with AD username and password, together with an additional form of verification, such as to enter a code from their phone or approve the login via the Microsoft Authenticator App for MFA. Once logged in, and authenticated via password and MFA, the user can then access the Virtual Network in Azure which in this case contains a Windows server file share and the user can work remotely outside the office.
- Virtual Network IP configuration
- Create VPN Gateway in Azure
- Network Policy Server install (NPS)
- VPN Policy for RADIUS in NPS
- Logging in NPS
- Test VPN connectivity from Windows 10 without MFA
- Azure MFA extension for NPS
- MFA Configuration for User Accounts
- MFA Conditional Access Policy
- Test VPN connectivity from Windows 10 with MFA
- MFA Logging
What is VPN Gateway
VPN Gateway FAQ
Download & install NPS extension for azure AD
MFA Manual Setup




