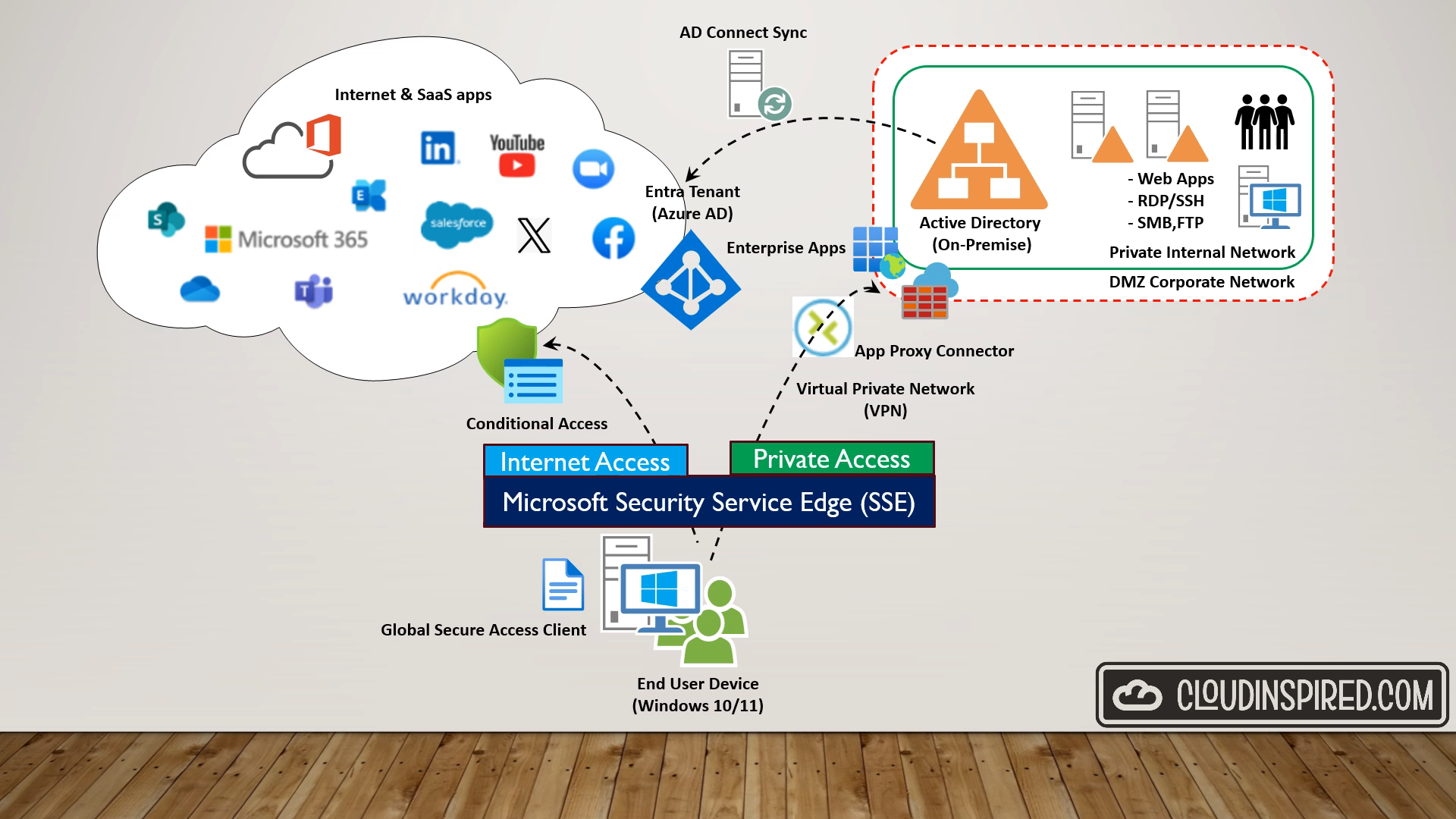
In this video we are going to give a step by step guide, deep dive and demo on Microsoft Entra Private Access and how to configure implement this solution
This is build on Zero Trust where we can connect users securely from any device and network to private apps on-premises and across any cloud. Giving granular access control to apps and separate at the user or device level and control access to private apps across any environment.
This reduces the need for legacy VPNs and traditional network access which doesn’t really scale to modern demands of cloud and the user experience isn’t great connecting via a VPN to our corporate network. Also its not really secure as once we have logged in over a VPN to our network perimeter and are in to our private network we normally have access to everything. Leaving it open to a attack from a compromised account or device and giving unnecessary access to everything within the perimeter.
So with zero trust… we trust no one and give least privileged access, all identities must be authenticated, authorized, and continuously validated before being granted access to company private applications and data.
If you didn`t catch the last video on Microsoft Entra Security Service Edge we talk about this approach in depth and look at at typical legacy network security approaches with office environments and cloud and what’s the need for this change to keep up with our flexible and modern ways of working with digital transformation and the way we secure access. Microsoft Entra Private Access is currently in public preview we can secure access to all private apps, resources and protocols from endpoints to secure all access using a zero trust model.